Cybersecurity is a vital aspect of any organization’s operations, but it can often be constrained by budget limitations. However, the good news is that there are several excellent free tools available that can bolster your cybersecurity arsenal and help protect your network. In this article, we will explore the benefits of utilizing free and open source software for cybersecurity purposes.
Transparency and Trust with Open Source
When it comes to free software, the question of trust naturally arises. Can you really rely on something that is provided for free? The answer is yes, especially if the software is open source. Open source development allows end-users to access and review the source code of the application, ensuring transparency and trust. Users can verify that the software does not engage in any malicious or deceitful actions with their data.
Furthermore, the open source model encourages users who are programmers themselves to contribute to the improvement of the software. They can modify the source code, fix bugs, or add new features. These changes are then submitted to the maintainers of the product, who incorporate them if deemed valuable. This collaborative approach benefits both the community of users and the developers, as the more eyes that review the code, the greater the chance of identifying and addressing bugs or vulnerabilities.
Read More: 5 Advantages of Using an Access Control System
However, it is important to note that open-source software is not entirely foolproof and can still have bugs. Nevertheless, the open-source community is known for promptly characterizing and addressing any identified issues. Users can access the source code as soon as bug fixes are available, allowing them to compile their personalized version of the software with the necessary patches. This ensures that critical fixes can be implemented immediately without having to wait for the official release.
Five Essential Open Source Tools for Cybersecurity
Now let’s dive into five vital open source tools that can significantly enhance your cybersecurity measures.
1. NMAP: A Powerful Network Mapping Tool
In today’s interconnected world, understanding the devices connected to your network is crucial for effective planning, security, and risk assessment. This is where NMAP, the network mapper, comes into play. NMAP is an advanced scanning and reporting tool that enables you to identify and gather essential information about the devices on your network.
Discover and Analyze Your Network
NMAP goes beyond simply detecting connected devices. It performs comprehensive scans to gather data such as the operating system type and version, open ports, IP addresses, and even devices connected via Wi-Fi. With its cross-platform compatibility, NMAP is available for Linux, Windows, and Mac computers, making it a versatile choice for all users.
Easy Installation and Usage
Installing NMAP is a breeze, especially for Ubuntu users. A simple one-liner command:
“sudo apt install nmap”

It’s all it takes to acquire and set up this powerful tool. Once installed, utilizing the "-h" command line option or referring to the manual page "man nmap" will provide you with comprehensive guidance and detailed information about various NMAP functionalities.
Advanced Scanning Options
To make the most of NMAP, you need to understand some essential scanning options. Three key options are commonly used:
1.Thorough Scanning (-T4): This aggressive scanning mode ensures that no stone is left unturned. It provides deeper insights into your network by performing a meticulous examination of connected devices.
2. OS and Version Detection (-A): This option enables NMAP to detect the operating system and software versions running on devices, making it easier to identify potential vulnerabilities and security risks.
3. Verbose Output (-v): NMAP can generate detailed reports, but with verbosity enabled, you get an even more comprehensive breakdown of the scan results. This information is invaluable for identifying and resolving any network issues.
Analyzing Scan Results
Once the scan is complete, you may find it overwhelming to digest the extensive amount of information generated by NMAP. Thankfully, you can redirect the output to a file by employing the following command:
nmap -T4 -A -v 192.168.1.0/24 > scan.txt

This captures the scan results in a convenient text file, allowing you to review them at your own pace.
To analyze the scan results, you can utilize the less command followed by the filename:
less scan.txt

This way, you can scroll through the detailed scan results and focus on the essential details provided for each device. For instance, let’s take a look at what NMAP discovered about the device with the IP address 192.168.1.15, which revealed the presence of four open ports.
Enhancing Scan Precision

If a device raises suspicion or requires further investigation, you can employ the `-T5` option, which initiates the most thorough and precise scan. However, keep in mind that this mode, commonly known as the “insane mode,” takes more time to complete due to its meticulous nature.
Through the power of NMAP, you gain unparalleled visibility into your network infrastructure. With precise information about your devices, you can make informed decisions regarding security measures, patching schedules, and network optimization. The extensive capabilities of NMAP empowers you to safeguard your network effectively and stay one step ahead of potential threats.
Read More: Google Chrome Version 74 & 75 – New Features and Possibilities for All Users
2. Wireshark: Unravel Network Traffic with Precision
While NMAP provides valuable device-level insights, understanding the actual network traffic within your infrastructure requires a different approach. Wireshark, a powerful packet capture and analysis tool, equips you with the ability to observe and interpret network communications between your devices.
Installing Wireshark
Wireshark, available for Windows, Linux, and Mac operating systems, offers a broad range of capabilities for network analysis. For Ubuntu users, installation is as simple as executing the command:
sudo apt install wireshark

During the installation process, you will be prompted to decide whether to enable packet capture for non-root users. Consideration must be given to the security implications of allowing non-root users such privileges, as it may compromise sensitive network information. Consequently, choosing to require root privileges when running Wireshark ensures network traffic remains private.

Capturing and Analyzing Packets
Once installed, launching Wireshark can be achieved with the command:
sudo wireshark

An array of network interfaces available for traffic capture will be displayed. Select the desired interface to commence packet capturing.

Wireshark’s user interface comprises three panes, with the top pane showcasing captured network traffic. By highlighting a packet in the top pane, you can explore its details in the middle and bottom panes. The middle pane provides convenient human-readable values presented in a collapsible tree view, while the bottom pane presents raw packet data in hexadecimal and ASCII formats.

Filtering the Data
Wireshark’s filtering capabilities are vital for refining your analysis and focusing on the information that matters most. While capturing everything without using filters is recommended to preserve all data, filtering becomes indispensable during the analysis phase. Filtering only during capture might inadvertently exclude valuable packets.
Here are some examples of Wireshark filters for targeted analysis:
To select packets involving the IP address 192.168.1.15 as either the source or destination:
ip.addr == 192.168.1.15
To select packets with 192.168.1.15 as the source IP address:
ip.src == 192.168.1.15
To select packets with 192.168.1.15 as the destination IP address:
ip.dest == 192.168.1.15
To filter packets exchanged between two IP addresses:
ip.addr == 192.168.1.15 && ip.addr == 192.168.1.24
To display all HTTP and DNS packets:
http or dns
To select TCP packets using port 4000 as either the source or destination:
tcp.port == 4000
To display all HTTP GET requests:
http.request
To find TCP packets containing the word techopedia:
tcp contains techopedia
By leveraging Wireshark’s robust filtering capabilities, you can narrow down your analysis to specific packets and gain insights into network behaviors and communication patterns.
Read More: How to Recover Deleted WhatsApp Messages without Backup on Android and iOS?
3. Osquery: Simplify Computer and Server State Discovery
In addition to network mapping and packet analysis, understanding the state of your computers and servers is crucial for maintaining a secure and efficient network environment. Osquery facilitates this by allowing you to query the state of your systems using simple SQL statements.
Wide Compatibility and Installation
Osquery is available for Windows, Linux, and Mac computers, ensuring broad compatibility across various platforms. To install Osquery on Ubuntu, navigate to the Osquery download page and acquire the appropriate “.deb” package file. Once downloaded, access the directory containing the package file and install Osquery using the command:
sudo dpkg -i osquery_4.6.0-1.linux_amd64.deb

With this straightforward installation process, you can quickly integrate Osquery into your system.
Embrace the Power of Osquery
To leverage the capabilities of Osquery, launch the interactive shell using the command:
osqueryi

The interactive shell response provides a prompt where you can enter SQL commands, ending each command with a semicolon (;) and pressing “Enter” to execute it.

For example, the following SQL statement retrieves usernames with a length of four characters:
SELECT username FROM users WHERE LENGTH(username) = 4;

Security-related queries can also be performed, such as examining the suid_bin table, which holds details about applications with the SUID (Setuid) and GUID (Setgid) bits set. Monitoring these binaries is important to detect any potential exploitation, as threat actors may abuse these elevated privileges for malicious activities.
SELECT path, permissions FROM suid_bin;

Through SQL statements, Osquery provides a flexible means to query and analyze the state of your computers and servers, enabling you to identify vulnerabilities, ensure compliance, and maintain a secure network infrastructure.
4. Nikto: Web Vulnerability Assessment Tool
In the world of cybersecurity, safeguarding corporate websites and portals is of paramount importance. This is where Nikto comes into play, offering an effective solution to identify and address various vulnerabilities. Developed by experts in the field, Nikto has the capability to:
Scan for potentially dangerous files and programs:
With an extensive database, Nikto can scan and detect up to 6700 potentially harmful files or programs, ensuring comprehensive coverage.
Identify outdated server versions:
Nikto’s advanced scanning capabilities extend to over 1250 servers, enabling the detection of outdated versions that may pose security risks.
Uncover version-specific vulnerabilities:
With its extensive knowledge base, Nikto can pinpoint version-specific issues on more than 270 servers, ensuring comprehensive vulnerability assessment.
Installation and Execution:
The installation process for Nikto is straightforward, particularly for Ubuntu users. By running the command:
sudo apt install nikto

You can quickly install Nikto on your system, making it readily available for use.
To gain practical experience in using Nikto, it is advisable to run it against a test website specifically designed with built-in vulnerabilities. It is important to note that Nikto’s thorough scanning process may take approximately 40 minutes or more, highlighting its comprehensive nature.
When executing Nikto, it is necessary to specify the webserver to be scanned using the -h (host) option. Additionally, the -o (output) option allows the user to define the filename for the generated report. Nikto intelligently determines the desired report format based on the filename extension, supporting CSV, HTML, TXT, and XML formats.
For instance, the following command initiates a Nikto scan on the specified website and generates a report in HTML format:
nikto -h https://www.webscantest.com/ -o report.html

While the scan is underway, real-time progress updates are displayed in the terminal window to ensure that the process is ongoing and not stalled.
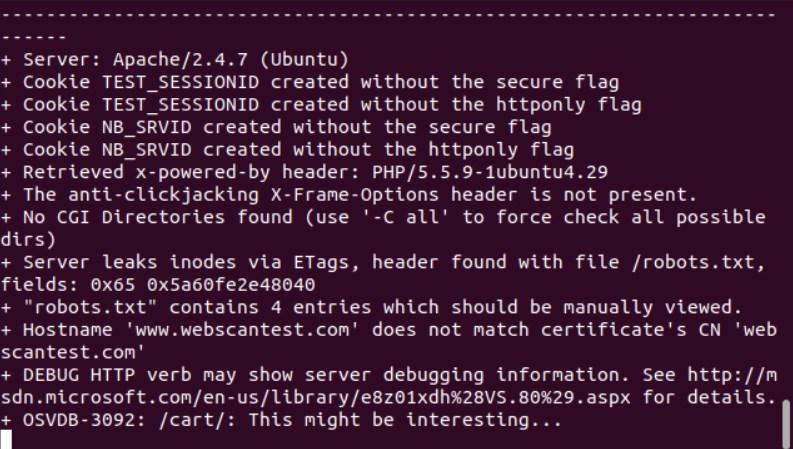
Upon completion of the scan, locate the saved report file and open it by double-clicking on the “report.html” file. The report will open seamlessly in your preferred web browser, providing valuable insights into the identified vulnerabilities.

5. Kali Linux: Your Ultimate Arsenal for Comprehensive Security Testing
For those seeking a comprehensive suite of tools to bolster their security measures, Kali Linux is a platform that should not be overlooked. Specifically tailored for penetration testing, Kali Linux offers an array of tools designed to evaluate and fortify your defenses against potential threats.
It is worth noting that the very tools that Kali Linux provides can be utilized by malicious actors, highlighting their popularity among cybercriminals. Nevertheless, this serves as a reminder of the importance of familiarizing oneself or the relevant individual within an organization with these tools. By doing so, one can effectively identify vulnerabilities within networks and websites, subsequently reinforcing security measures.
To leverage Kali Linux’s capabilities, it is recommended to download an ISO file and install it as a virtual machine using a hypervisor like VirtualBox. This approach ensures a seamless and isolated environment for security testing purposes.
Kali Linux comes pre-loaded with essential tools such as Wireshark, Nikto, nmap, along with an extensive range of reconnaissance, attack, and exploit tools. This eliminates the hassle of manually gathering and installing individual tools, allowing users to focus on the critical task at hand.
Noteworthy Tools and Frameworks:
Among the array of tools and frameworks incorporated into Kali Linux, a few notable ones stand out:
1. The Metasploit Framework:
This comprehensive suite of tools is specifically designed to identify and exploit vulnerabilities. Powered by a vast database containing over 140,000 common vulnerabilities and more than 3,000 exploits (CVEs), the Metasploit Framework provides a powerful arsenal. Developed by Rapid7, this offering is available both as a free and open-source solution, as well as a commercial product with professional support.
2. Burp Suite:
With a primary focus on web-based applications and general website security, Burp Suite is an indispensable penetration testing tool. Originally an open-source version, Burp Suite offers a comprehensive range of features alongside its commercial counterpart.
3. The Social Engineering Toolkit:
The Social Engineering Toolkit (SET) empowers users to conduct social engineering attacks encompassing phishing and spear-phishing. While primarily intended for susceptibility testing within an organization, the ease of accessibility serves as a stark reminder of the potential dangers of such software.
User-Friendly Interface and Versatility:
Kali Linux is built on the Debian distribution and employs the XFCE desktop environment by default. Even when operating within a virtual machine environment, users will find Kali Linux to be highly responsive, quick, and intuitively designed.
Navigating through the main system menu grants users access to an array of top-tier categories, providing a seamless exploration of available software and tools.

Image by Freepik

